LetsDefend’s DFIR Challenge: Ransomware Attack Walk-Through

LetsDefend has released a new DFIR challenge to investigate a ransomware attack. I will walk you through the digital forensic investigation and how to find the answers to the questions. I will also try to explain my thinking as the investigation unfolds, so you can understand how I came to my conclusions. Attempt the challenge on your own first, but If you get stuck then refer to the guide.
Investigation Prep-work
Before we can begin we need to set up a tool called Redline produced by FireEye. Redline is a free tool that can gather system details and create a memory dump file of a system after an incident. Redline collects data about processes, temp memory, drivers, registry, and other crucial data to determine what happened in the breach. So we will need to download the tool and install it. I recommend setting up a VM(6x CPU, 8GB RAM, 64GB HDD, OS-Win10) to do all this work within, but that is optional. Download and install the tool then continue.
URL: https://www.fireeye.com/services/freeware/redline.htmlRedline Data Analysis
After installing the Redline tool download and extract the LetsDefend “Memory Dump” file. Open Redline and open the now extracted “AnalysisSession1.mans” file.
Review the questions the LetsDefend challenge is asking. We want to have an idea of what data we need to find. The questions will provide us with some meta-game details that could be very helpful.
- Please find the dropped DLL, include the whole path including the DLL file.
- What is the MD5 hash for the DLL?
- What is the name of the ransomware note that got dropped?
- What is the URL that the initial payload was downloaded from? (Include the whole URL with the payload)
- The ransomware drops the copy of the legitimate application into the Temp folder. Please provide the filename including the extension
- What is the name of the ransomware?
Based on the questions we should keep an eye out for a malicious DLL file and a ransom note, likely a TXT file. Question #5 tells us the attack is likely a DLL Side-Loading attack to load the malware.
Where to start?
If this is your first time using Redline it may be overwhelming at first. I suggest you take some time to poke around the menus and get comfortable with the layout. When you are ready, start by looking at the basic system information. Since we know nothing about this system we need to gain an understanding of the environment, purpose, and users of the system.
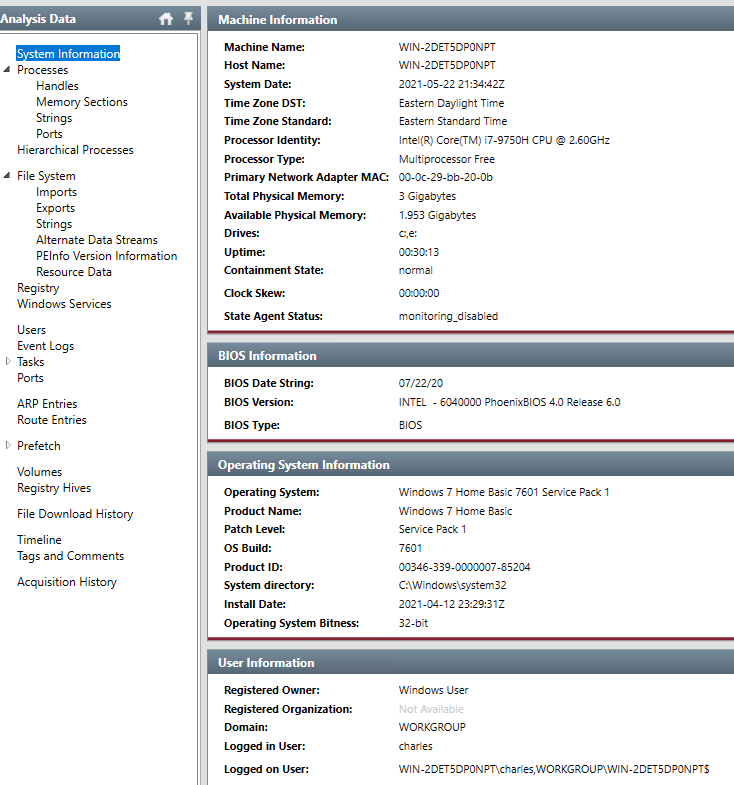
In the above image we can see that we are on a Windows 7 Home Desktop, not domain joined, 32-bit OS, and the username is “charles”. The CPU tells us this is a modern laptop(2019). It is unlikely a modern laptop would be running Window 7 32-Bit edition, so this is a VM.
Running Processes
I prefer to start my investigations by reviewing the processes running on the infected system. There is a high likely hood the malware would have been running at the time the system image was created. So we should find evidence of the malware, which may lead us to additional evidence of how the infection occurred.
Head to the “Processes” tab in the right-hand menu. Look through the process list and add a “Follow-up Required” tag to any processes that look odd. Look for processes the have signs of being compromised. Things like EXE files running from %APPDATA% or %TEMP% folders, oddly named EXE file name(i.e. explorer-2.exe), BAT, VBA, CMD, etc. files running. It takes some experience to be able to spot what is normal and what may be abnormal.
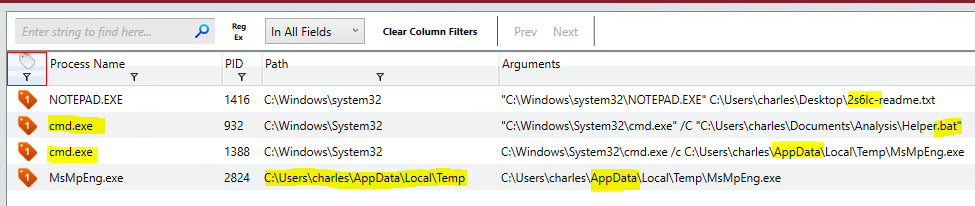
A review of the processes showed a few processes that looked odd, and a few I was just not sure about what they do. The real stand-outs here, to me at least, is the following.
- Notepad++ has a file named “2s6lc-readme.txt”. Maybe the ransom note?
- “cmd.exe” process running the “Helper.bat” script. (This turned out to be not malicious)
- “cmd.exe” calling a sub-process MsMpEng.exe from an %APADATA% folder. BIG RED FLAG!
Ransomware Note
Ransomware always leaves a note so the extortionist can let the victim know how to contact them for payment. The notes left behind are usually pretty unique to the ransomware group, MAZE, DarkSide, Netwalker, etc. each have their own distinct notes. We can gather a lot of data about the attackers and the malware by analyzing the ransomware note.
Open the “File System” tab from the right-hand side menu. In the search box type name of the text file that was opened by notepad; “2s6lc-readme.txt”.
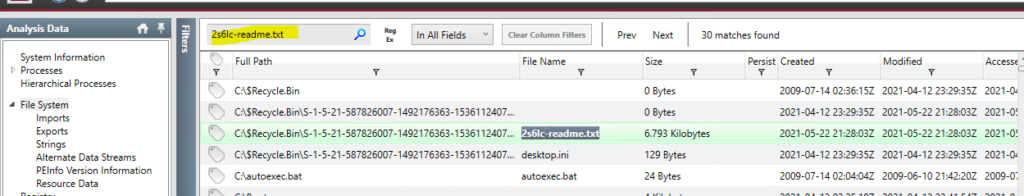
Double-click on the text file found, then from the bottom toolbar that appear select “Strings”. This will display the whole ransomware note.
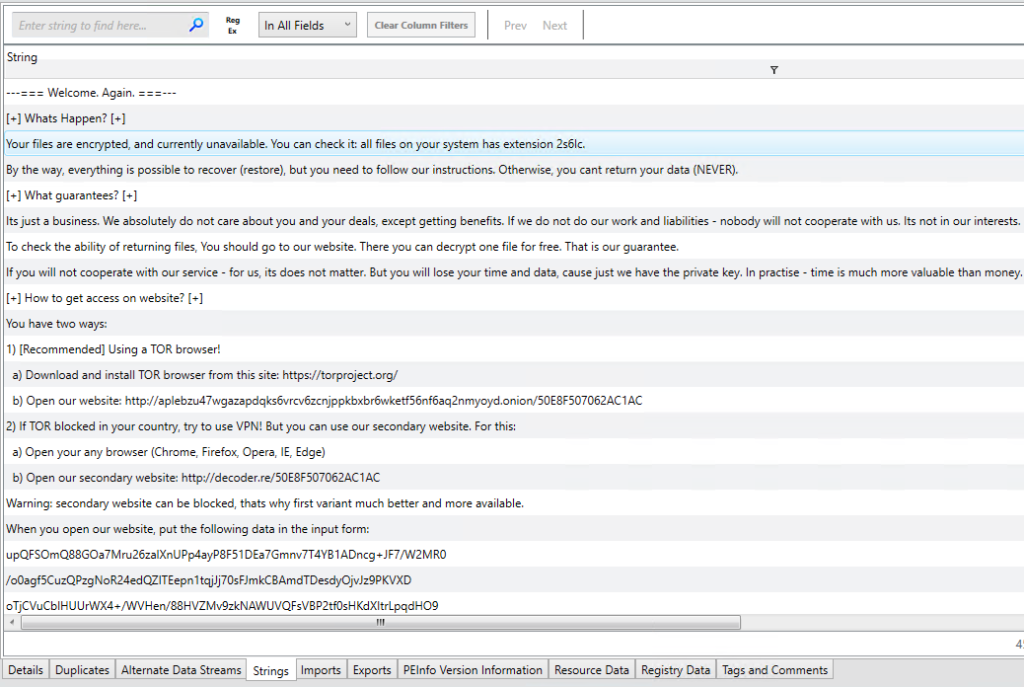
Text Format
---=== Welcome. Again. ===---
[+] Whats Happen? [+]
Your files are encrypted, and currently unavailable. You can check it: all files on your system has extension 2s6lc.
By the way, everything is possible to recover (restore), but you need to follow our instructions. Otherwise, you cant return your data (NEVER).
[+] What guarantees? [+]
Its just a business. We absolutely do not care about you and your deals, except getting benefits. If we do not do our work and liabilities - nobod ill not cooperate with us. Its not in our interests.
To check the ability of returning files, You should go to our website. There you can decrypt one file for free. That is our guarantee.
If you will not cooperate with our service - for us, its does not matter. But you will lose your time and data, cause just we have the private key n practise - time is much more valuable than money.
[+] How to get access on website? [+]
You have two ways:
1) [Recommended] Using a TOR browser!
a) Download and install TOR browser from this site: https://torproject.org/
b) Open our website: http://aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd.onion/50E8F507062AC1AC
2) If TOR blocked in your country, try to use VPN! But you can use our secondary website. For this:
a) Open your any browser (Chrome, Firefox, Opera, IE, Edge)
b) Open our secondary website: http://decoder.re/50E8F507062AC1AC
Warning: secondary website can be blocked, thats why first variant much better and more available.
When you open our website, put the following data in the input form:
upQFSOmQ88GOa7Mru26zalXnUPp4ayP8F51DEa7Gmnv7T4YB1ADncg+JF7/W2MR0
/o0agf5CuzQPzgNoR24edQZITEepn1tqjJj70sFJmkCBAmdTDesdyOjvJz9PKVXD
oTjCVuCblHUUrWX4+/WVHen/88HVZMv9zkNAWUVQFsVBP2tf0sHKdXItrLpqdHO9
ydmsxEyDipyEMpLDnMBQsZqQzNz4xAWiiGGEpTgQzbZXFWK4t5ybYdnPRi3urjVp
tAxQVi5PjIQF7bWaGON0mFt1MHLUOSxGhMSqdZmc9Wgc1TZRLIfcgz7XEulqFNnS
EFVqYoXgZYSTOKeuhy4nv9VUQimZUYg14irGZzj2qZS7Q4aCES30UCDYfoH7yCx8
ok5fzzjcCq4uU48EgW4NHGQb2ZUUOePC+JIm57ME8QrcdL13r/qYirbv768OHY13
agu8w3WyP4gc2iEH6Tu3lWPBNcM/GKoHqBY+fZdqBbGg463Q2r+2w80I7RN8/r6R
lY4z+401+hh7xIYTMrc+0WzDFVypYchn6j4qDaFiSsxdNA6dvymyIY3qvlTxLh7Z
APlSluWzklxJ8P7aQNhc07vLpmBaE5KAkd6UhA+MD+14uqcfePE6JT+OA2wwuYWt
5qvWO7d3A4X5UmJThH6+3OZ41gEir3eFspyO2mbSmPWOHAa1QHuBkzBq4Doxdjn3
gPLy0+YK8zdkF4WWeZb4gdJBlAgVvBBqoPLRKnHkK4f0DQFdw322VUffgj+/l9G+
52U5e7s64CHPCP28Jnw3Y2H95kht0vv/yoh/KnCe2V1L1QmDJPQ2BOq4Ccl/Qi08
8b5y10ruuLAPKTAp7DmXIy09TMUXrxNlHWydnuL2HC6Bfjt5OYG+W8yhlNaOa+wd
jAGOwBiFOpraHYbILO0T1uEbJvxnz6dOUA+saFwo6qhLJ/YKnHyhCxVpX4lIH833
UK7hrH75fbnohKHSRIBNLO9s2+6VGdbXLEzgwO/wnmGBpzUFrN8fwGZpSNDM1I4C
oAVT8S62D8eFYSWaq1len+p8vonNBXXrFC2C+01m95aNQa2YdS0pFd48E88Aq4bF
cdsDclPXhuiw4pLeRV0/IcKTCITZZy974VNTrRMbRoryYe34rblkyH6jqb+TSsXx
hgxmZvjWtCU2uuxlGQZCCTzEP5KlCgOGL2aS+gHrg4LMZHBn3/W/Q6wdDtj9bKhi
ji74P3TlH8hCrl7pXZPqOQQ5au/xrdV39sxM+DHpzkgmRNzJHKJWzwmL7c1dovcr
NvP1NGJpSRQcvduLTQIreIMvLWaYczXcwOoC8JgtOMaYHg==
-----------------------------------------------------------------------------------------
!!! DANGER !!!
DONT try to change files by yourself, DONT use any third party software for restoring your data or antivirus solutions - its may entail damge o the rivate key and, as result, The Loss all data.
!!! !!! !!!
ONE MORE TIME: Its in your interests to get your files back. From our side, we (the best specialists) make everything for restoring, but pleas hould not interfere.
!!! !!! !!!Googling a few lines of the file tells us the ransomware group behind this attack is Sodinokibi, AKA REvil, AKA Sodin. Having the name of the ransomware group means we can now search for IOCs related to the groups, making the malware easier to find.
This ransom note also answers questions 3 and 6!
MsMpEng.exe – Microsoft Malware Protection Engine
Moving on to the likely executable that encrypted the system. The “MsMpEng.exe” launched as a child process of “cmd.exe”. This is not normal, so to examine it go to the “File System” tab, and search for “C:\Users\charles\AppData\Local\Temp\”. This will highlight everything in that directory.
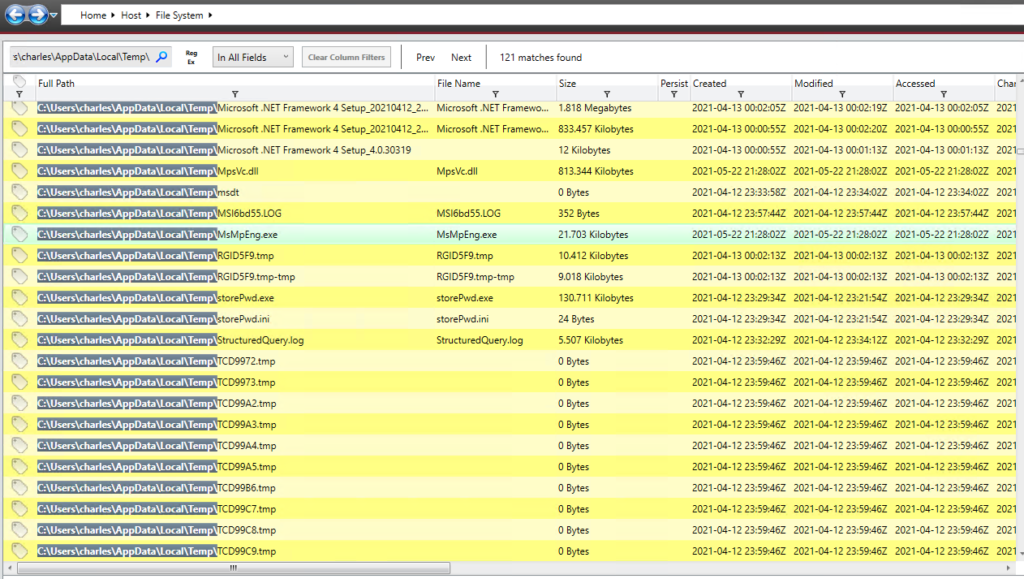
Double-click on the “MsMpEng.exe” file to see the details of the file.
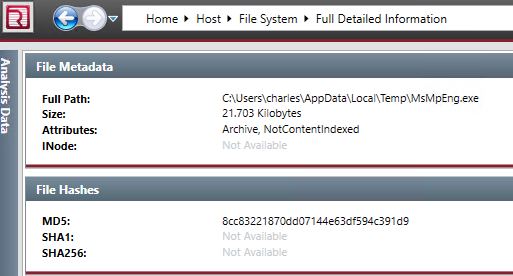
Copy the file MD5 hash and search Virus Total with the files MD5.
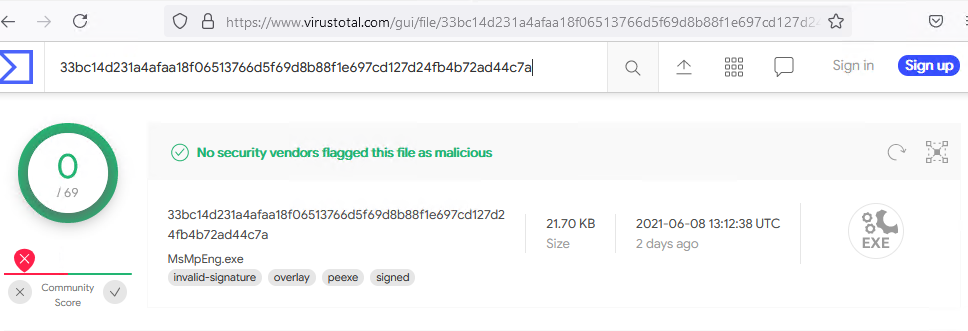
The “MsMpEng.exe” file looks clean, but we know there must be something malicious with the executable. This executable should not be running in the %TEMP% folder. The “MsMpEng.exe” is the Microsoft Malware Protection Engine, a part of the Windows Defender system, and should be running from the “C:\Program Files\Microsoft Security Client\” folder. So how can an authentic Microsoft signed executable be misused to exploit a system?
DLL Side-Loading Exploit
To understand how the authentic “MsMpEng.exe” executable was misused, I need to explain how DLL Side-Loading works. The basic idea is to use a signed well known executable file, and trick it into loading a DLL file that contains malicious code we want to run.
Windows executable files look for the DLL files it requires at runtime. When it searches for these DLL files it will first check its current working directory. When executing “C:\Users\charles\AppData\Local\Temp\MsMpEng.exe” it needs a DLL, for example, named “KERNEL32.dll”, the directory “C:\Users\charles\AppData\Local\Temp\” is searched first for the “KERNEL32.dll” file. If one is found it is loaded into memory; no other checks required. If a DLL Side-Loading exploit is used, we should find a malicious DLL in the same directory as the EXE file.
To find the DLL files the “MsMpEng.exe” executable is using click on the “Imports” tab at the bottom of the full file details page.
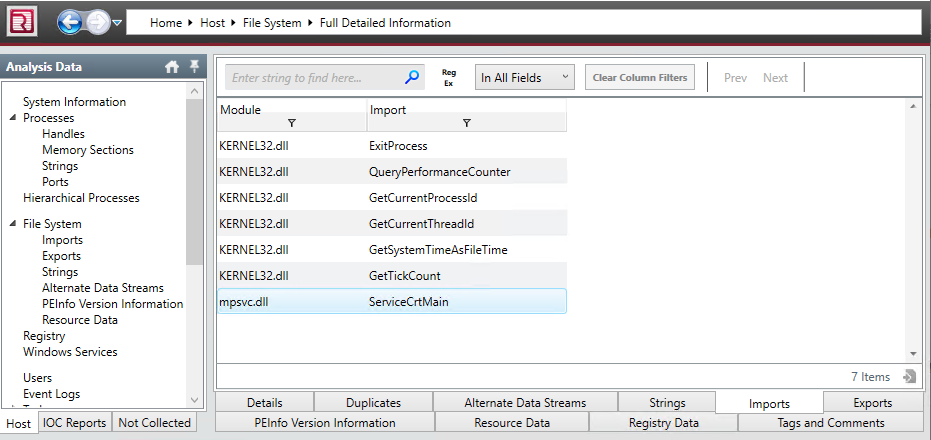
“MsMpEng.exe” imports two DLL files; “KERNEL32.dll” and “mpsvc.dll”. We will need to search the same folder directory(“C:\Users\charles\AppData\Local\Temp\”) for DLL files with a matching name. If we find either “KERNEL32.dll” or “mpsvc.dll” in the same %TEMP% directory then they are probably malicious.

Sure enough we find “mpsvc.dll”. We now need to get a MD5 of this file and search Virus Total.
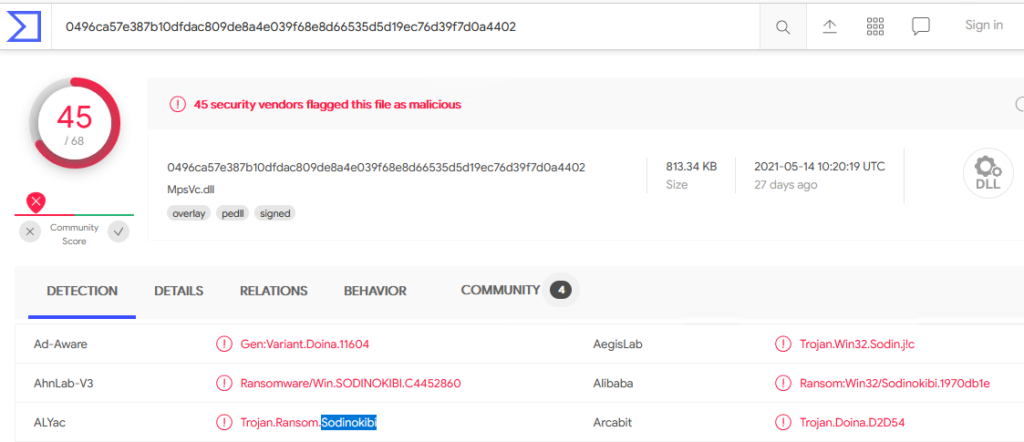
What a surprise, it’s malware!
We now can answer questions 1, 2, & 5!
Timeline of Events
Now that we have discovered a part of the malware we can start to work backward to how it got on the system. The mpsvc.dll is a Trojan, for backdoor and persistence on the system. Meaning it was put there by another piece of malware; a “Dropper”. We need to find the Dropper malware. Dropper malware normally establishes itself right after getting access to the system. In theory, the “mpsvc.dll” file would have been created just after the Dropper malware was run. With this knowledge, we can work backward from the “mpsvc.dll” file creation event to the Droppers creation event. To do this we will use the “Timeline” tab from the right-hand menu. Find the “mpsvc.dll” file creation event by adding a filter to the “field” column with the string “Created”. Then use the search box with the string “C:\Users\charles\AppData\Local\Temp\mpsvc.dll”.
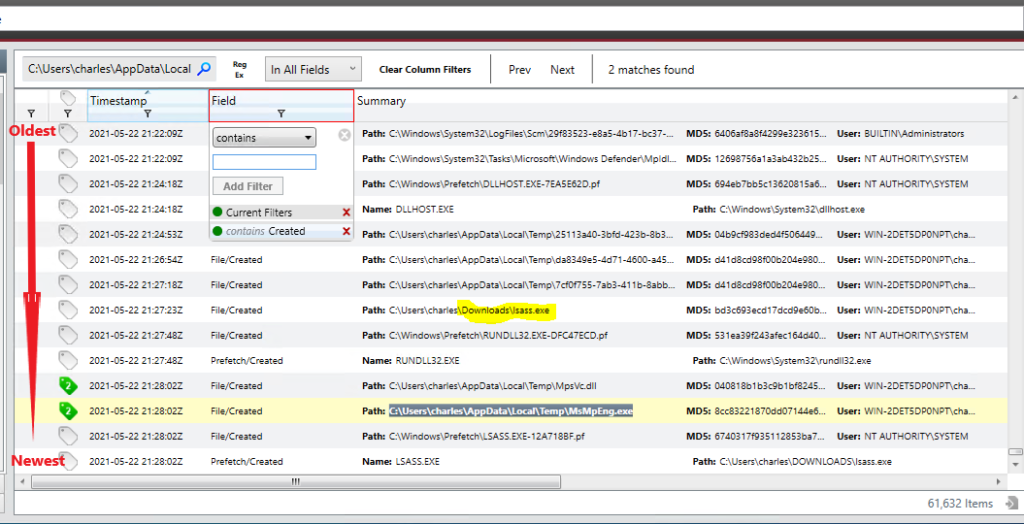
The timeline shows a file created just before the creation event of “mpsvc.dll”; “C:\Users\charles\Downloads\lsass.exe”. The “lsass.exe” is “Local Security Authority Subsystem Service”, a executable built into Windows. It is not something anyone should be downloading. This may be our Dropper malware. Let’s gather some data about the file.
Grab the “lsass.exe” file’s MD5 hash and search Virus Total
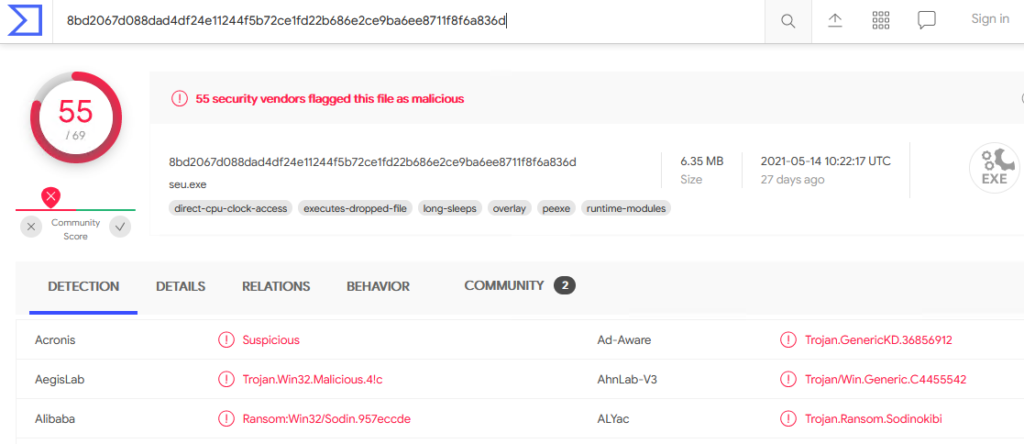
Virus Total confirms the file is malware and it’s classified as a Dropper Trojan.
Where did you come from?
We have found the Dropper Trojan(“lsass.exe”) that started the infection. We need to now discover how it got on the system in the first place. Since the malware was in the User Downloads folder we can make a guess it was downloaded with a web browser.
Open the “File Download History” tab from the right-hand menu. In the “File Name” column add a filter for “lsass”.
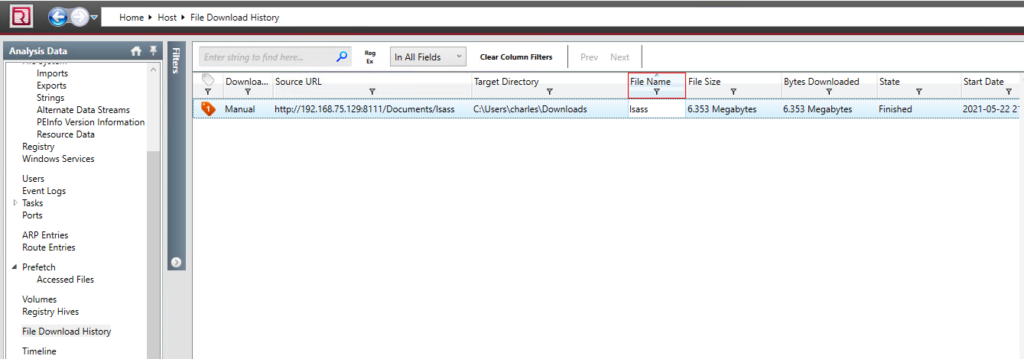
We have located the original source URL that the malware came from. Additionally, there are details showing that the user “charles” downloaded the malware using Chrome v89.0.4389.114.
We now can answer question 4!
Incident Response Postmortem
This DFIR comes from a simulated event, but let’s treat this as if this was a real event. What have we learned from this incident and how can we protect ourselves in the future?
What were the security gaps, and how can we fix them?
- A user account was able to download and run malware.
– This could have been stopped if the “charles” account was not in the “Administrators” group. Creating a separate User and Administrator account will prevent any process from running privileged tasks without express permission. - Anti-Virus did not detect the malware.
– An up-to-date AV would have caught this malware and stopped it. Even when I copied the raw text of the ransom note, my forensics system’s AV started alerting; no malware just the notes text! - Running an outdated Operating System.
– This is a common thread in most malware infections today. Windows 7, Server 08(R2) are very insecure by today’s standards. - Other internal systems in the network are compromised since the malware was downloaded from IP “192.168.75.129”.
– This infection traces back to another internal system. If all our systems had HID Agents, or a NID monitoring the network we could have caught an abnormal internal HTTP request. - The user account “charles” is compromised, or the owner of the “charles” account is a malicious insider.
– If the “charles” account was compromised we need to investigate further how that happened.

