Hardware 2FA Yubikey 5s Review
Two-Factor Authentication(2FA) should no longer be optional in an enterprise environment. It must be a requirement. 2FA breaks most attack chains and helps prevent privilege escalation and credential harvesting. With a properly implemented 2FA system, attacks on User’s credentials are no longer scalable and require significantly more time and effort. In my opinion, the new standard should be, at a minimum, all Domain Admin level accounts in Active Directory must be using 2FA. Once an adversary attains Domain Admin level rights, it is game over for the rest of the network. Only a complete and total rebuild of all systems can restore security integrity.
There are many products on the market to secure a network using 2FA. Software-based 2FA involves a rotating time-based pin code, Text message codes, or even just email verification. The issue I see with software-based 2FA is they all are online and may be vulnerable to attack. Several successful 2FA attacks were able to steal secret software tokens to generate one-time keys. The other issue is an incorrect implementation of the 2FA system. For these reasons, I prefer hardware-based two-factor authentication systems over software-based.
Short on time? TLDR
Why Software 2FA is Weaker, Source List
- Chinese hacker group caught bypassing 2FA
- cPanel 2FA bypassed in minutes via brute-force attacks
- 6 most common ways attackers bypass 2FA

The hardware-based 2FA I have come to rely on is Yubikeys. There are a ton of features in the new YubiKey 5 series. To start, you can enforce that the user must touch the key when authenticating, ensuring the user intends to perform the login. The key also supports a variety of different 2FA functions all with one key. The NFC connection feature is what sold it for me. NFC-enabled phones can quickly scan a YubiKey 5s to authenticate.
Hardware Yubikeys One-Time-Pass(OTP)
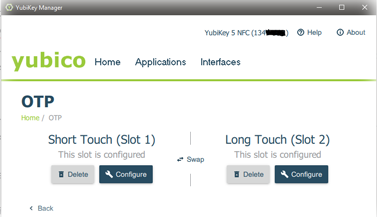
The Yubikeys One-Time-Pass(OTP) function generates a 32 character time-based password that the user does not need to enter or interact with. The password passes over to the application it is authenticating to automatically. The YubiKey’s OTP function has two configuration slots. So two different OTP methods can be active on the same key. You can configure one slot for local computer user login for a non-AD Windows PC, and the second slot for a Challenge-Response OTP key for your KeePass database. You can utilize one OTP slot to authenticate with multiple third-party applications, as long as they are using the same OTP method.
The two OTP slot limitation is a drawback. The various ways vendors implement OTP is not always compatible with other vendors. For example, KeePass’s Challenge-Response OTP is not compatible with Bitwarrdens OTP. So if you use OTP slot #1 for local computer login, you have to choose between Bitwarden and KeePass for slot #2. You can, however, set up Bitwarrden using OATH OTP to work around this limitation. It would be nice to see the number of OTP slots doubled to four in future products.
OATH Time-Based Rotating OTP Key
YubiKeys are also able to generate OATH time-based rotating One-Time-Passwords. OATH tokens are only 6 to 8 digits long. Users entered the time-sensitive code into the application they are authenticating to before the timer runs out. The OATH OTP 2FA method has the most widespread support with vendors and products. This method is not as strong as the above-mentioned 32 characters time-based OTP password but is still very secure.
YubiKey’s implementation of OATH is more secure and flexible than phone apps like Google’s Authenticator, Authy, and other purely software-based OATH programs. The Yubikey stores OATH token keys in the key hardware itself, and not in a phone or computer. You cannot extract OATH Token keys from the Yubikey. So removing a Yubikey from a system also removes the token keys. This protects you from lost or stolen devices compromising your 2FA.
Since the OATH token keys are on the Yubikey hardware, the keys are now portable between your phone and computer. Making it very easy to set up token keys on your computer, and then being immediately able to use those token keys on your phone. YubiCo has an OATH Authenticator application for pretty much every platform, Windows, Linux, MacOS, Android, and iOS.
PIV SmartCards
The YubiKey for 2FA in an Active Directory environment relies on Certificates. This is just like deploying a Smart Card infrastructure but with the Smart Card and Smart Card Reader all in one. Setting up, or enrolling, a new user’s key creates a private key and stores it within the Yubikey. The Yubikey can hold multiple signed certificate keys for authenticating a user. The documentation says it can hold up to 24 certificates, but I have only tested with up to four certificates myself. When logging into Windows you will have the option to select the identity(cert) you want to log in as. A 6 to 8 digit pin protects the certificates on the YubiKey. If you fail to enter a pin correctly 3 times the YubiKey deletes the stored keys. This prevents malicious use of a stollen YubiKey.
To use a YubiKey in an enterprise environment there are multiple other components we need to understand and have already set up. The infrastructure required for a YubiKey deployment is complicated, with a steep learning curve. If you are not a Windows CA PKI and Active Directory expert, you are going to have a hard time. This is where the YubiKey, in my opinion, came up short.
There is documentation on their website, but not a clear path from start to finish to implement YubiKeys in a domain environment. You will need to read in between the lines and connect the dots yourself. If this is your first deployment, you will need to read through all the Wiki pages on the website. I also recommend deploying in a lab environment first too. To compound this issue, some of the deployment How-Tos are not the correct way to deploy production Certificate Authorities(CA). Correctly deploying a CA is a project in and of itself. Once you do deploy YubiKey and the infrastructure required it will make authentication into systems a much faster and simpler process. It will take time but it is worth the deployment headache.
TLDR: Too Long Didn’t Read
The YubiKey is a well-designed product for 2FA. Depending on the type of 2FA you are going to use, deploying the YubiKey can be very difficult, or very easy. The comfort of being able to physically control your access credentials cannot be understated. You can lock down your accounts and remove the burden of remembering long and complex passwords.
This key will become a part of your everyday. The checklist in your head of items you need before leaving the house, wallet, keys, cell phone, will now include YubiKey. When I first got mine, there were a few times on my drive to work that I had to turn around to go back for my YubiKey. Overall, the Pros outweigh the Cons, and I would recommend the YubiKey.
Pros and Cons
Cons
- Smart Card Deployment requires a lot of existing knowledge and experience in Windows CA, PKI, Kerberos, and Active Directory.
- The YubiKey’s Wiki has all the data but it can be challenging to form a clear understanding of what is needed. YubiCo or someone really should make a video training course.
- You have to make sure the YubiKey goes everywhere with you. If you lose it or forget it you’re going to have a bad day.
- There are only 2 OTP slots. That limits how many products you can use a YubiKey with.
Pros
- Peace of mind. You can physically hold the keys to your digital kingdom.
- Simplifies and speeds up the login process. No more 32 character passwords to remember!
- Requiring a person to touch the key before the YubiKey will give out credentials. Ensuring software cannot just access the keys any time it wants.
- It will stop 99.9% of attacks on your logins! I am guessing at the percentage here, but it really will break almost all credential attacks.

