How to Investigate Malicious DNS Requests
DNS requests are a treasure trove of information about your environment. While I could talk at length about the details gleaned from a network’s DNS requests, I want to instead focus on how to investigate malicious requests coming from an internal IP. Security products like Cisco Umbrella or DNSFilter are great at identifying an internal IP requesting known malicious domain names. However, they lack the ability to tell you what within that system is making the request.
So we are going to discuss methods of identifying system processes making malicious DNS requests.
It May Not Be Malware
Before we continue, I want to point out a few things to keep in mind during your investigation.
A malicious DNS request does not mean the system is definitely infected. There are many reasons for a system to make malicious DNS requests and not be infected with malware. Here are some other potential causes for seeing malicious requests.
- Visiting sketchy websites, like Torrent sites, Adult content, Hacking sites, etc.
- Running a crypto miner.
- Torrenting.
- Bad web browser plugin/addons.
- Drive-By Malware ads
- Freemium App/Software or games.
The point is there could be a hundred reasons malicious DNS requests are occurring, so don’t jump to conclusions.
Setup Sysmon to Monitor DNS Requests
A default Windows installation has the ability to do some DNS logging, but it is not helpful. The default DNS logs will only show that a DNS query was made, but we need more details. To get useful logs with detailed information, we need to install Sysmon.
System Monitor, AKA: Sysmon
Windows has awful event logging, but Sysmon can fix that issue. Sysmon is a system service and device driver that gives Windows detailed logging for certain types of events. If you ever want to have any idea of what happened on a system you need Sysmon.
You can read more about Sysmon at the below URL.
https://docs.microsoft.com/en-us/sysinternals/downloads/sysmonInstalling Sysmon
1. Download Sysmon
To get started, head to the below URL and download the zip file with the Sysmon installer in it.
https://download.sysinternals.com/files/Sysmon.zipOnce downloaded extract the “sysmon64.exe” file. You do not need to keep the “sysmon64.exe” file after installation, but I recommend you do. If you want to reconfigure Sysmon or uninstall it you will need this file. For this reason, I recommend copying the “sysmon64.exe” to the Windows directory(C:\Windows\).
2. Create Sysmon DNS Config file.
We need to create the XML file that will control Sysmon. Sysmon’s default DNS logging configurations do not fully log DNS queries. This is because the DNS logging is noisy and adds unnecessary resource usage.
To enable full DNS logging in Sysmon we need to add a configuration file that will exclude DNS queries from being filtered, meaning we will log all queries.
Create an XML file “C:\Windows\config-dnsquery.xml”, and fill the config file with the below configurations.
<Sysmon schemaversion="4.21">
<EventFiltering>
< onmatch="exclude" />
</EventFiltering>
</Sysmon>3. Install Sysmon with the DNS Config File
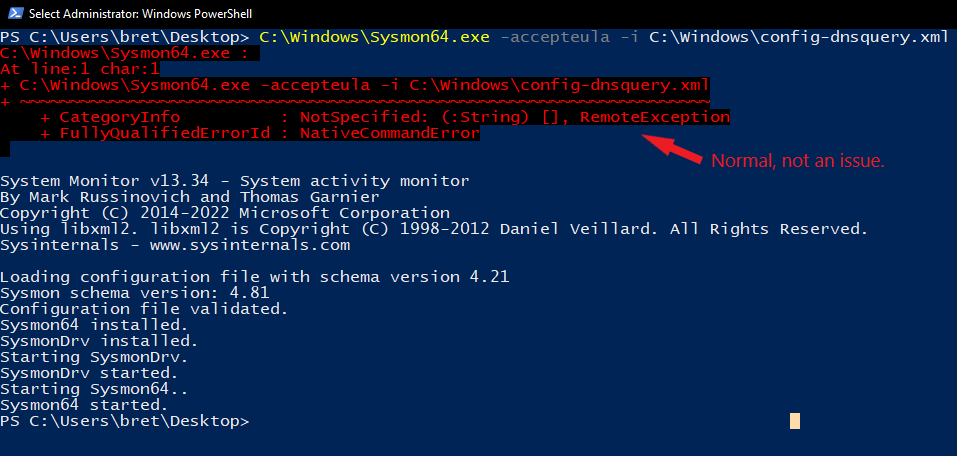
At this point you should have two files in place; “C:\Windows\sysmon64.exe” and “C:\Windows\config-dnsquery.xml“. We will now use these two files to install Sysmon.
Open a PowerShell terminal as an Administrator, then run the following command.
C:\Windows\Sysmon64.exe -accepteula -i C:\Windows\config-dnsquery.xmlThis command will install Sysmon with our DNS config. There is no need to reboot the system, Sysmon is installed and running at this point.
Log DNS Review
Now that we have Sysmon installed and logging we just need to review the logs for the malicious domain name. To review the logs do the following.
- Open Event Viewer.
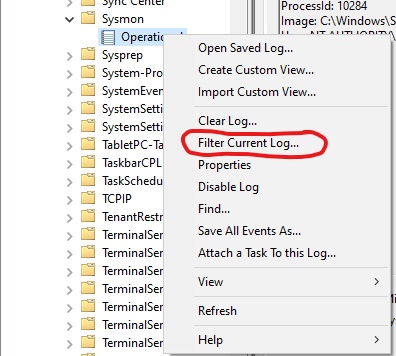
- Navigate to “Applications and Services Log > Microsoft > Windows > Sysmon > Operational”
- Right-click the “Operational” log and click “Filter Current log…”
- Filter for Event ID #22.
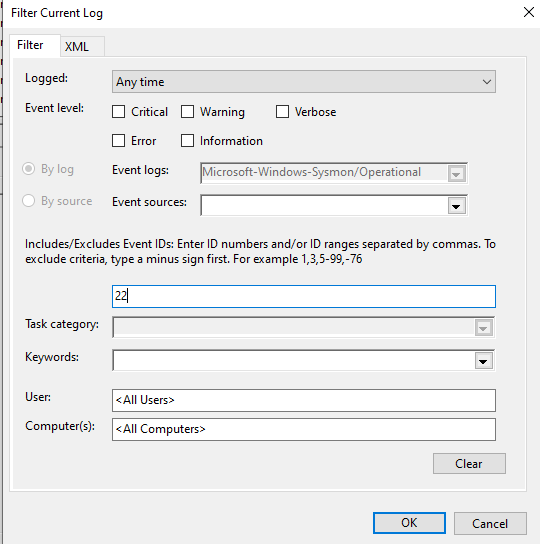
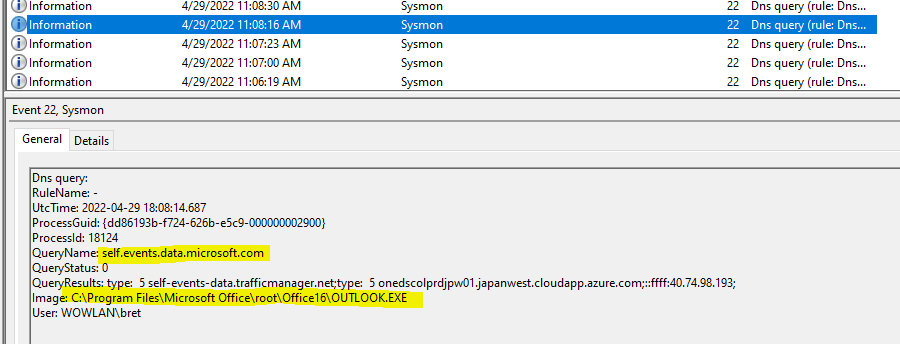
Now we can search through the log and see the executable that makes a DNS request.
The DNS event above shows us that “OUTLOOK.EXE” requested the DNS resolution of the domain name “self.events.data.microsoft.com”. So we are now able to track down the exact executable requesting a DNS record. This is used to hunt down system processes making malicious DNS requests.
Searching Sysmon DNS Logs with PowerShell
Manually searching logs for a malicious domain name is dumb! Let’s work smarter and not harder by using PowerShell to search the logs.
# The malicious Domain Name to look for.
[string]$DomainName = 'malware.com'
# The number of hours back in time to look at.
[int]$HourBackToSearch = 2
# Search the event log.
Get-WinEvent -FilterHashtable @{
Logname = 'Microsoft-Windows-Sysmon/Operational'
ID = 22
StartTime = [datetime]::Today.AddHours(-$HourBackToSearch)
EndTime = [datetime]::Today
} | Select-Object -Property Message | Where-Object {$_ -like "*$DomainName*"} | Format-ListBonus!
Like I said before, manually doing things is dumb. So I have uploaded my personal script that automates this entire process, installing, configuring, and searching for malicious DNS requests. Check out the PowerShell script on my GitHub.
https://github.com/Brets0150/CG_BlueTeamTools/blob/main/SysmonDnsLogging.ps1