Windows Client Hardening
Securing & Blocking Malicious DNS Requests
Domain Name Resolution(DNS) translates domain names like “google.com” to an IP address of “8.8.8.8” so computers can understand where things are on the Internet. Most malware, spam emails, and malicious websites rely on DNS. By filtering out malicious DNS requests we can prevent malware from calling home or downloading more malware. Luckily, such a filtering service exists for free. QUAD9.net runs a free service that monitors malicious domain names and will block those DNS requests. All we need to do is configure our computer’s DNS servers to use QUAD9 and block any other DNS server from being used.
To set the QUAD9 DNS servers run the following in an Administrative PowerShell prompt.
Windows PowerShell
Get-NetIPConfiguration | Foreach IPv4DefaultGateway | Set-DnsClientServerAddress -InterfaceIndex {$_.ifIndex} -ServerAddresses 9.9.9.9,149.112.112.112 ; ipconfig /all 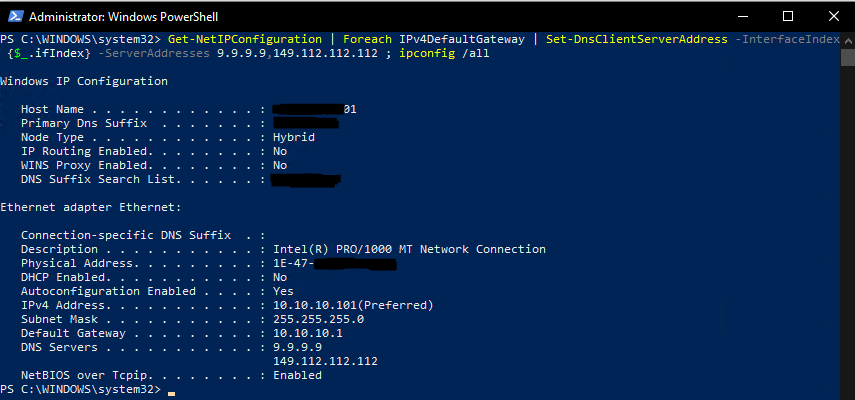
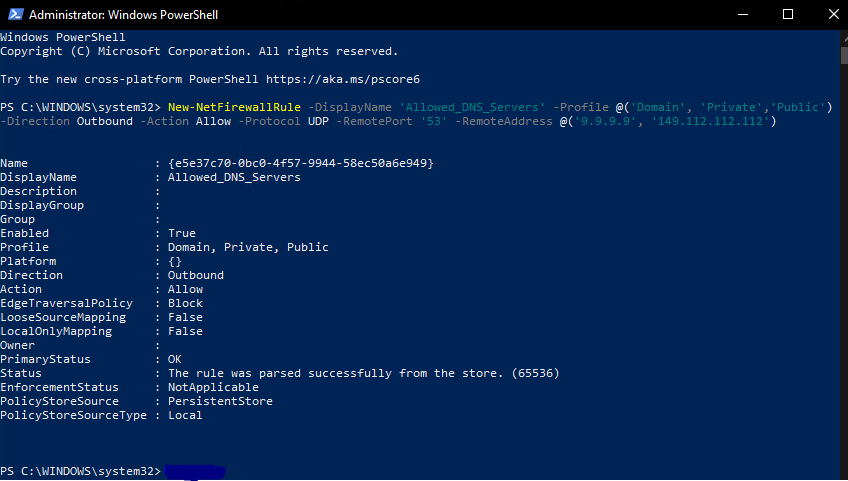
Now we need to prevent any other DNS service from being used for DNS resolution. We can do this by setting up a firewall rule that will only allow DNS requests with a destination of IPs 9.9.9.9 & 149.112.112.112.
Run the following in an Administrative PowerShell prompt.
Windows PowerShell
New-NetFirewallRule -DisplayName 'Allowed_DNS_Servers' -Profile @('Domain', 'Private','Public') -Direction Outbound -Action Allow -Protocol UDP -RemotePort '53' -RemoteAddress @('9.9.9.9', '149.112.112.112')